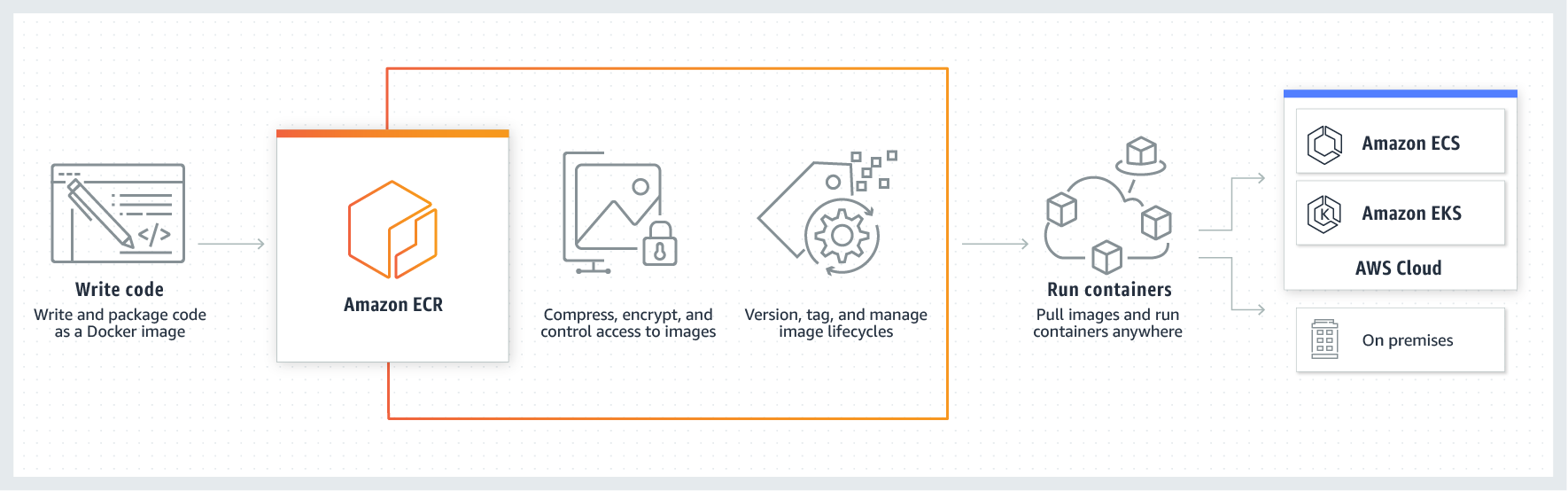
As you can see Configuring AWS credentials and profiles in Windows is straightforward. Profiles make the process of interacting with different AWS accounts extremely easy as it allows switching between user contexts using a simple command. Both the AWS CLI and AWS PowerShell modules allow passing in a profile name parameter that makes this easy. The default profile is the first profile you establish with the aws configure command. Additionally as shown with the environment variable, you can override the profiles configured. The AWS CLI supports named profiles so that you can quickly switch between different AWS instances, accounts, and credential sets.
Let's assume you have two AWS accounts, each with an access key id and a secret access key. The first account is your default profile, and the second account is used less often. When you first run "aws configure" command it sets that user as default user of AWS CLI. You can validate the same in the credentials file as well. But we might need to use multiple users to access our AWS services. For example, some users may have only read access to S3 or some users may have access to Dev resources and others to Production resources. If you have a need for multiple profiles, you can create as many as you'd like using the Set-AWSCredential command.
This command allows you to specify your access key and secret key similar to what you have done with the Initialize-AWSDefaultConfiguration command. But instead of creating a default profile, it will create a profile with whatever name you specify. Once you have finished the installation you need to configure it. You'll need your access key and secret key that you get when you create your account on aws.
You can also specify a default region name and a default output type (text|table|json). To update these settings, run aws configure again (with or without the --profile parameter, depending on which profile you want to update) and enter new values as appropriate. The next sections contain more information about the files that aws configure creates, additional settings, and named profiles. You can configure additional profiles by using aws configure with the --profile option, or by manually adding entries to the config and credentials files. For more information on the config and credentialsfiles, see Configuration and credential file settings.
The AWS CLI --profile option can be used to add new clusters to your ~/.kubeconfig. By adding named profiles, you can switch between Kubernetes contexts without needing to export new AWS environment variables. You can create and use additional named profiles with varying credentials and settings by specifying the --profile option and assigning a name. When authenticating to AWS, AWS always recommends using profiles. They are a secure and more manageable way to pass credentials to AWS services.
Credentials like an access key and secret key can be independently managed on a per-command, per-session or all-session basis. You truly can get pretty granular with credentials with AWS PowerShell commands. We can save all of these references to commands or sessions in profiles that are saved on your local computer. These profiles are what stores your access and secret keys for use by the AWS commands. You'll need to enter your access key id and secret access key here as well as your default region. This will create a default profile using these credentials.
Are you looking to configure a workstation to work with your AWS environments? Do you have multiple accounts with and need to shift between the various AWS environments working with the AWS CLI or AWS PowerShell? We will look at the tools you need to have installed in Windows to work with AWS credentials in Windows effectively. We have installed AWS CLI on our machine and configured it for multiple users using profiles. Now we are ready to access different AWS services using the command line. In the next tutorial, we will learn to create new users from AWS CLI. Until then keep learning.
When you execute aws configure command without any argument, you'll be configuring aws credentials as your default profile. In order to see which your default AWS CLI profile is, run theaws configure list command. The command shows the name of the default profile, the profile's security credentials and region. Setting the environment variable changes the default profile until the end of your shell session, or until you set the variable to a different value. You can make environment variables persistent across future sessions by putting them in your shell's startup script.
For more information, see Environment variables to configure the AWS CLI. The docker group is created but no users are added to it. Continue to Post-installation steps for Linux to allow non-privileged users to run Docker commands and for other optional configuration steps.
In order to keep autocomplete fast, we do not make use of any of awsumepy's modules or any pkg_resources slow entry points. However, this means that any plugins that supply profiles won't be able to supply autocomplete with their profile names. To circumvent this, we utilize an autocomplete file located at ~/.awsume/autocomplete.json. When you pass the --refresh-autocomplete flag to awsume, it makes the calls to all plugins to collect all profile names together into that file. This will automatically install the aws plugin when you open a new shell. It gives you access to a few new commands and adds current aws profile to your prompt by default.
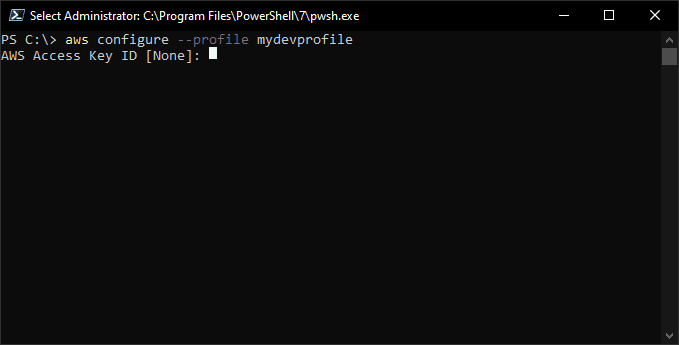
Once you've got the aws tool installed locally, you'll want to log in to your AWS accounts. To do so, you'll need an AWS user with Programmatic access enabled as well as your access key id and secret access key. AWS CLI setting up multiple profilesIn the above image, you can see that, using –profile option we can create multiple profiles like admin and s3_read. I have used the same credentials for both users but you get the idea of creating multiple profiles.
Continue to Linux postinstall to allow non-privileged users to run Docker commands and for other optional configuration steps. Let's say you only have a single access key to authenticate to AWS. You can create a default profile using this single access key. For example, one way to define a default profile is to use the Initialize-AWSDefaultConfiguration command.
When run, this command creates a profile called default that's used by all AWS commands in all sessions. You may have one or more PowerShell AWS profiles defined, but the simplest configuration is using a single default profile. Using a single default profile can be used if you only have a single access key and will always use that. You can target a specific region to awsume with the --region flag. This basically amounts to setting the AWS_REGION and AWS_DEFAULT_REGION environment variables.
Useful for overriding the region found in a config profile. If you want to connect to a different AWS acount from your CLI, then you can change your existing default profile credentials by executing the "aws configure" command again. The credentials file stores your API access key and secret access key.
You can specify one default profile that is used when no profile is explicitly referenced. Other profiles have names that you can specify as a parameter on the command line for individual commands. Alternatively, you can specify a profile in the AWS_PROFILE environment variable which overrides the default profile for commands that run in that session.
A named profile is a collection of settings and credentials that you can apply to a AWS CLI command. When you specify a profile to run a command, the settings and credentials are used to run that command. Multiple named profiles can be stored in the config and credentials files.
In this article, we looked at how to use boto3 and how it is built internally. We examined the differences between clients and resources and investigated how each of them handles pagination. We explored how waiters can help us poll for specific status of AWS resources before proceeding with other parts of our code.
We also looked at how collections allow us to perform actions on multiple AWS objects. Finally, we explored different ways of providing credentials to boto3 and how those are handled using IAM roles and user-specific access keys. "Per-session" credentials are not stored across your PowerShell sessions. Instead, they are temporary and removed when the session closes. Creating per-session profiles is nearly identical to creating all-session profiles. You'll still use the same Set-AWSCredential command but this time don't use the StoreAs parameter.
You'd simply run Set-AWSCredential -AccessKey $accessKey -SecretKey $secretKey and the temporary profile would be created. I guess nothing makes you as paranoid as deep sysadmin experience. First of all, you have to configure the aws-cli with named profiles.
If you haven't done so, the aws-cli documentation will guide you through this in a few easy steps. Due to the way AWS IAM and the local environment works, if you invoke your lambda functions locally using the CLI command serverless invoke local -f ... The IAM role/profile could be different from the one set in the serverless.yml configuration file. Thus, most likely, a different set of permissions will be in place, altering the interaction between your lambda functions and other AWS resources. An additional profile can be added using the aws configure command with the --profile option.
– This contains the credentials information when we just used 'aws configure' command without any parameter. – This section indicates that these value belong to the default profile. Keep in mind that you can have more than one profile configured, which will allow you to execute AWS cli commands against different AWS accounts as shown in examples below.
The config and credentials files on your machine - have the lowest precedence - lower than environment variables and command line options. In this case the name of the default profile is set using the AWS_PROFILEenvironment variable, which has higher precedence than the settings in thecredentials file. To use a named profile for multiple commands, you can avoid specifying the profile in every command by setting the AWS_PROFILE environment variable at the command line. You can use AWS_DEFAULT_PROFILE to switch between your multiple accounts by setting the default profile in your environment with CLI or SDK. AWS-CLI profile management on your local desktop can be a hassle.
Especially if you frequently switch between different accounts. Keeping track of available profiles, switching between them and knowing which one you're using at the time is tedious. Setting up named profiles helps a little bit but it doesn't take you all the way.
I personally don't like the –profile argument, I'm too lazy to use that. The AWS_PROFILE overrides the profiles configured with the aws configure command. The first command is equivalent to aws configure --profile default, which overides the default profile. The list option in the aws configure command will display the information about the current profile as shown below. The aws configure set command can be used to set a single configuration value in the AWS config file.
You can retrieve any credentials or configuration settings you've set using aws configure get. Specify the profile that you want to view or modify with the --profile setting. You can set any credentials or configuration settings using aws configure set. Command line options - have the highest precedence and override any environment variables or configuration stored in config and credentialsfiles. The installation script requires root or sudo privileges to install and use Docker.
If you want to grant non-root users access to Docker, refer to thepost-installation steps for Linux. Docker can also be installed without root privileges, or configured to run in rootless mode. For instructions on running Docker in rootless mode, refer torun the Docker daemon as a non-root user . (You can also manually add new profiles and access keys directly into ~/.aws/credentials).
Enter the Access Key, Secret access key, default region name, and default output format. Here I do not specify a default region, so we need to specify it explicitly while querying AWS services. I wanted to note the existence of the default profile, since this is the default behavior. But since this guide is about managing multiple AWS accounts, we're going to create custom profiles for each account. In this case your Lambda function is run locally and has not been deployed yet.
So any calls made in your Lambda function to any other AWS resources on your account will use the default AWS profile that you have. You can check your default AWS profile in ~/.aws/credentials under the tag. In such a case, we need to configure AWS CLI with multiple users using profiles. We can run configure command with –profile to set profile for users.
Managing multiple profiles for AWS CLI is super easy and it comes in really handy when you have to deal with multiple AWS accounts or IAM user accounts. In this article, I will show you how you can easily use AWS CLI commands using different AWS accounts. If you are unsure where your CLI is pulling your credentials or configuration settings from, look at the Location column when calling aws configure list. This ProfileName parameter is common across all AWS cmdlets. We now have two profiles created called default and Work with Work being the actual default one.
Your default profile will always be used unless overridden by another profile. At this point, you can run any AWS command you wish and if the access key and the secret key are correctly configured, they will work without error. When authenticating programmatically , you need to have an access key and secret key. These two keys allow you to authenticate as a certain user.
























No comments:
Post a Comment
Note: Only a member of this blog may post a comment.